Application Control
Application Control
Kodas: 11210Y1Kaina 1525 € su PVMŠią prekę turime sandėlyje.GamintojasHeimdal Security-
Application ControlThe simplest way to control application executionsApplication management solution for whitelisting and blocking of running applications. Customize live sessions, log everything on the go, and prevent users from running malicious software.



Prevent any unauthorized application execution.
Effortless IT management.
Multiple ways to allow or block apps
App Control allows users to allow or block application execution in more than one way: file path, publisher, certificate, vendor name, software name, MD5, and more. The choice is yours.
Automatic approval or denial flow
Accelerate your application approval or denial flow for system files with default ruling. Create or modify flows for individual users or AD groups.
Dual Modes Operation
Layers upon layers of granularity. Application Control operates in both active and passive mode. Take control of your user’s session or sit back, and let App Control weave its magic.KEY BENEFITS
Unique Solutions for Advanced ProblemsCombining App Control with Access Governance
Full-throttle your session application execution with additional access governance features by combining your App Control module with Privileged Access Management. App Control over PAM, allows for highly customizable admin sessions, giving you weapons you need to protect sensitive memory areas, hinder lateral movement inside your network, and safeguard your business assets.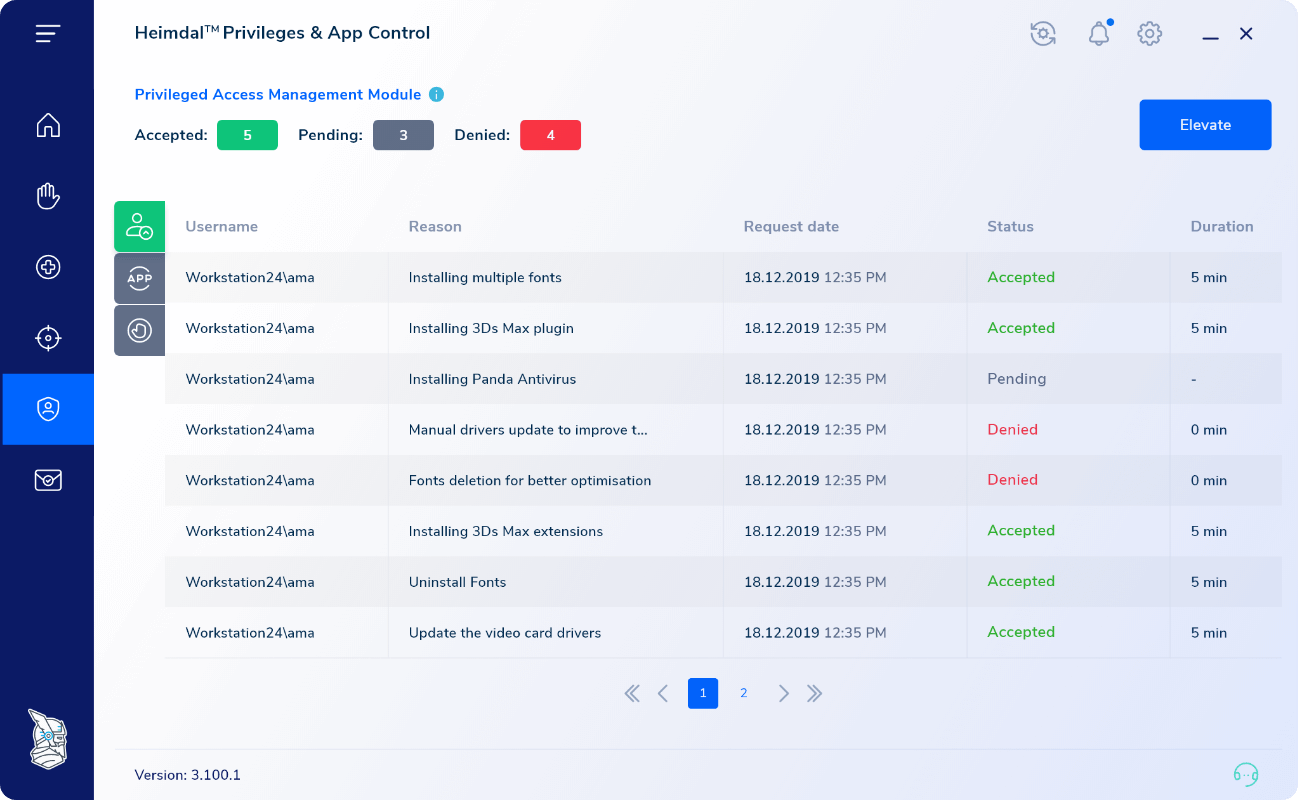
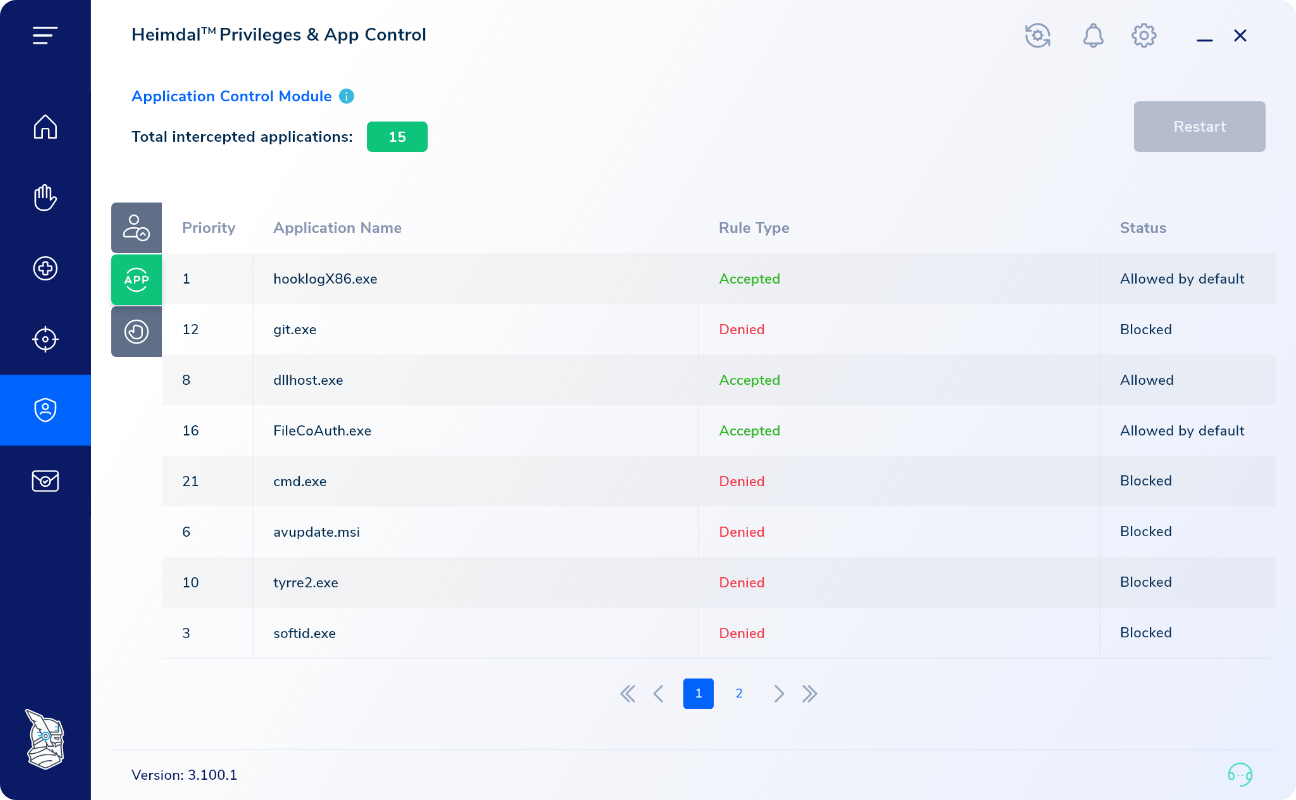 Extended audit trail
Extended audit trail
Explore new reporting features. App Control’s reporting module can help you gain additional insight into your elevated user session – applications opened, processes elevated per session, parent processes called, services requested, and more. Streamline your app/approval denial flow with historic executions, a feature that allows you to customize future elevated sessions by analyzing past sessions.Ease-of-use
App and process manipulation are usually done through a remote access tool. Get rid of the middleman and leap straight into the action. Use Application Control’s passive mode for live, rule-based, monitoring or define the rules yourself. Every byte of collected info is fed directly to your dashboard, where you can review the session’s details, further adjust user interactions parameters, request logs, and more!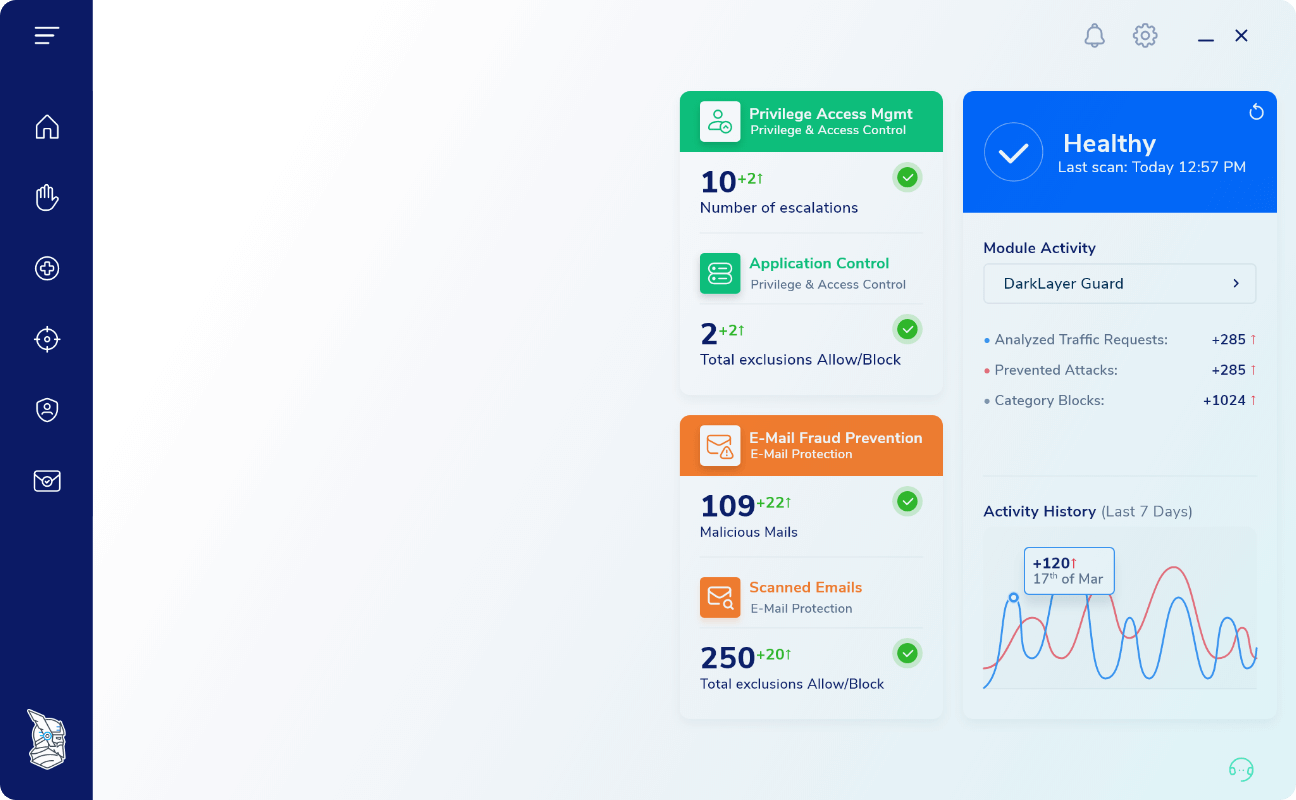
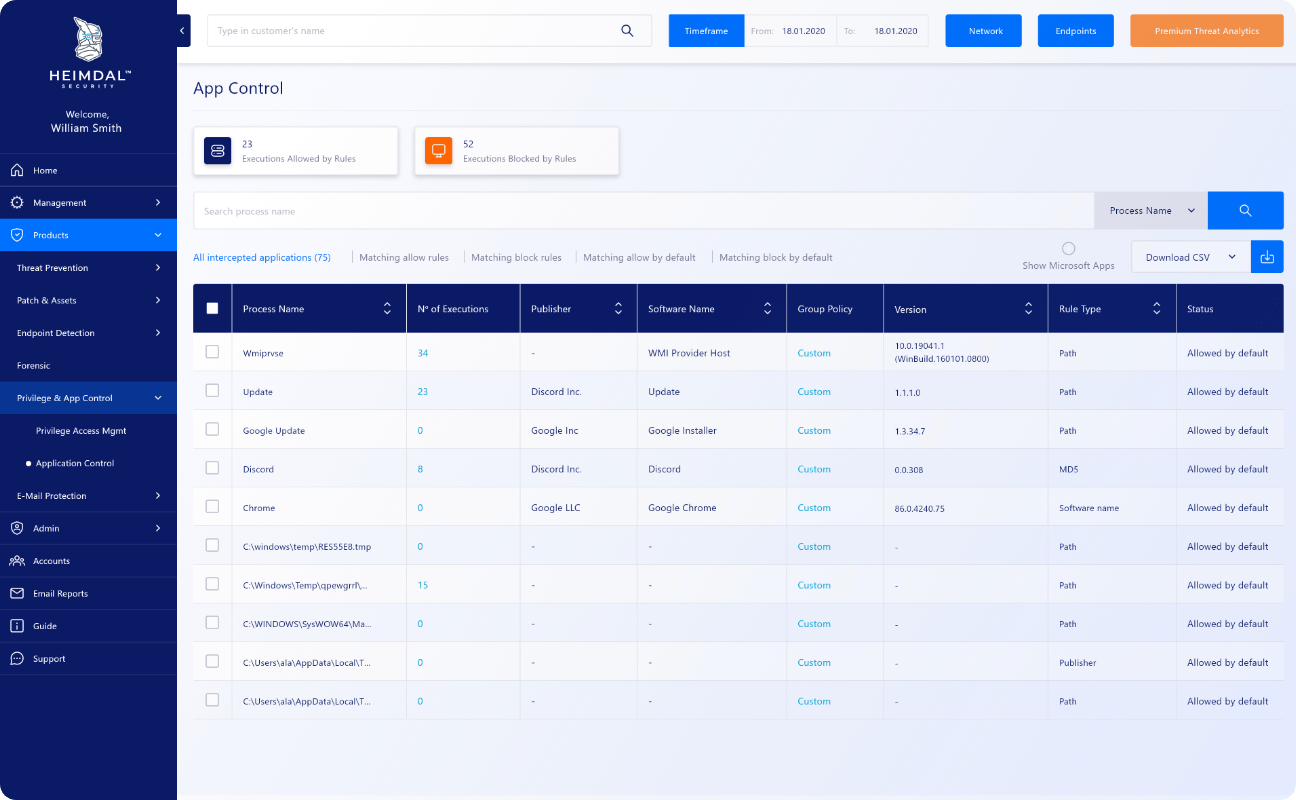 Productivity Overhaul
Productivity Overhaul
Say ‘goodbye’ to obsolete, endpoint-based tools with complicated licensing options and scalability issues. Application Control will ensure that your flows are enforced throughout the entire organization, giving you peace of mind and time to focus on other vital, organizational areas. Remove permanent rights and give access to application execution, when users need it. Application control also supports a full audit trail of Allowed Executions, Blocked Executions and Passive Mode monitored executions.
Remove permanent rights and give access to application execution, when users need it. Application control also supports a full audit trail of Allowed Executions, Blocked Executions and Passive Mode monitored executions.CENTRALIZED COMMAND CONTROL
One Unified Dashboard To Rule Them All.
TThe centralized dashboard unlocks the full potential of your threat-hunting engine and cyber-stance. Crisp graphics, intuitive controls, ready-to-download security status reports, ROI outlooks, mitigated threats, CVEs, and more conveniently stacked into a responsive and unified dashboard.