Email Fraud Prevention
Email Fraud Prevention
Kodas: 11150Y1Kaina 1997 € su PVMŠią prekę turime sandėlyje.GamintojasHeimdal Security-
Email Fraud PreventionPrevent Business Email Compromise and fraud attempts125 vectors of analysis coupled with live threat intelligence allows you to identify and stop Business Email Compromise, CEO Fraud, phishing and complex malware before compromise.



Prevent Email Fraud.
Never worry about fraudulent invoices and CEO impostors.
Fight back against e-fraud
Heimdal™ Fraud Prevention takes the fight to the hackers. Regain your piece of mind by protecting your email accounts against Business Email Compromise and Vendor Email Compromise attacks.
Advanced email scanning technology
Using 125 vectors of analysis to safeguard your email accounts and business assets. No more surprises waiting for you in the inboxes.
Multi-language support
Hackers will attempt to get around your defenses by various means, including language changes. Fraud Prevention by Heimdal™ supports multiple languages, increasing the detection accuracy for email alteration.KEY BENEFITS
Unique Solutions for Advanced ProblemsIncrease ROI, Decrease BEC chances
Directly reduce monetary loss as a result of fraudulent invoices. Reduce mail fraud as a result of CEO imposters and negative brand impact.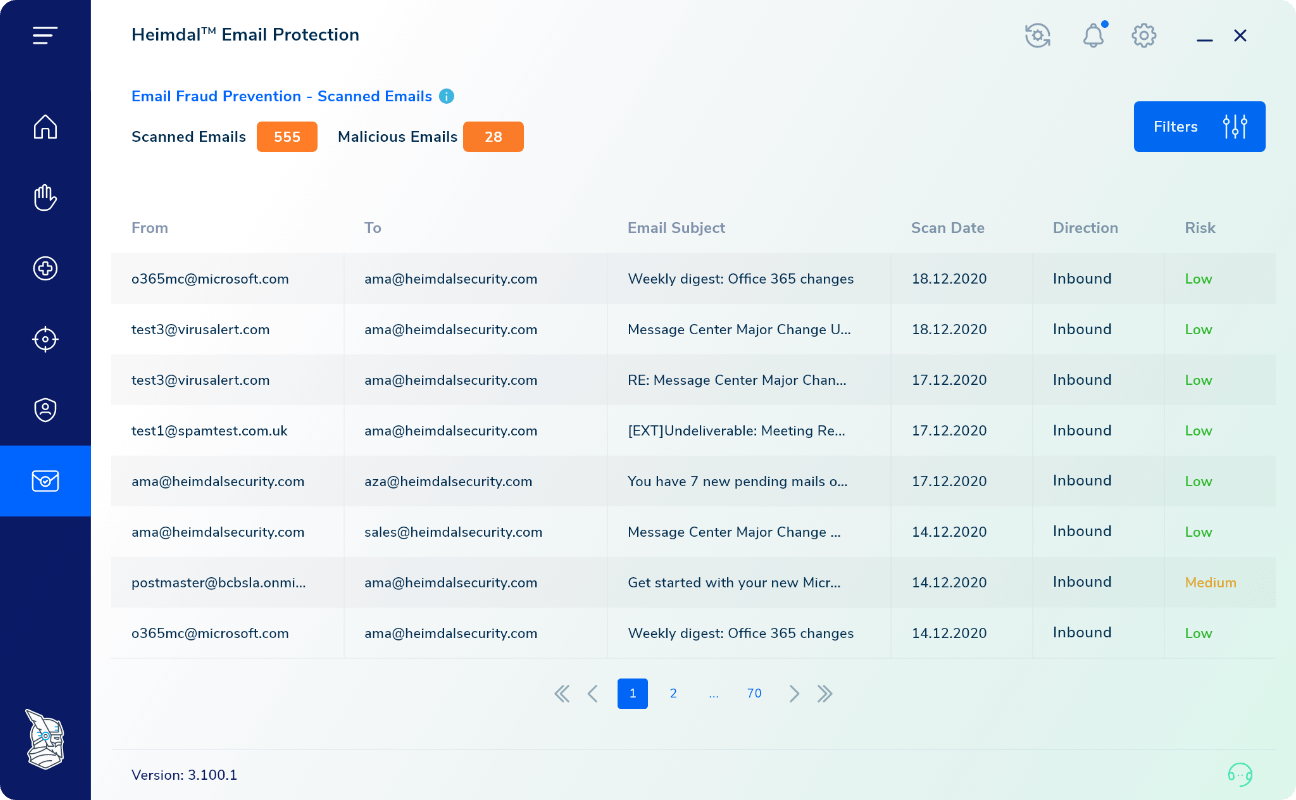
 Machine Meets Human Expertise
Machine Meets Human Expertise
Combining automatic scanning for email account compromise and fraud detection with human expertise, Heimdal™ Fraud Prevention can identify and stop attacks before they cause your business any damage.Decrease work load
Avoid needing to complicate all procedures endlessly for verbal and written double-checks with all people involved. You can never be too careful, but you can’t turn all operations into bureaucratic nightmares, drowned in additional signoffs, checking and re-checking of all variables.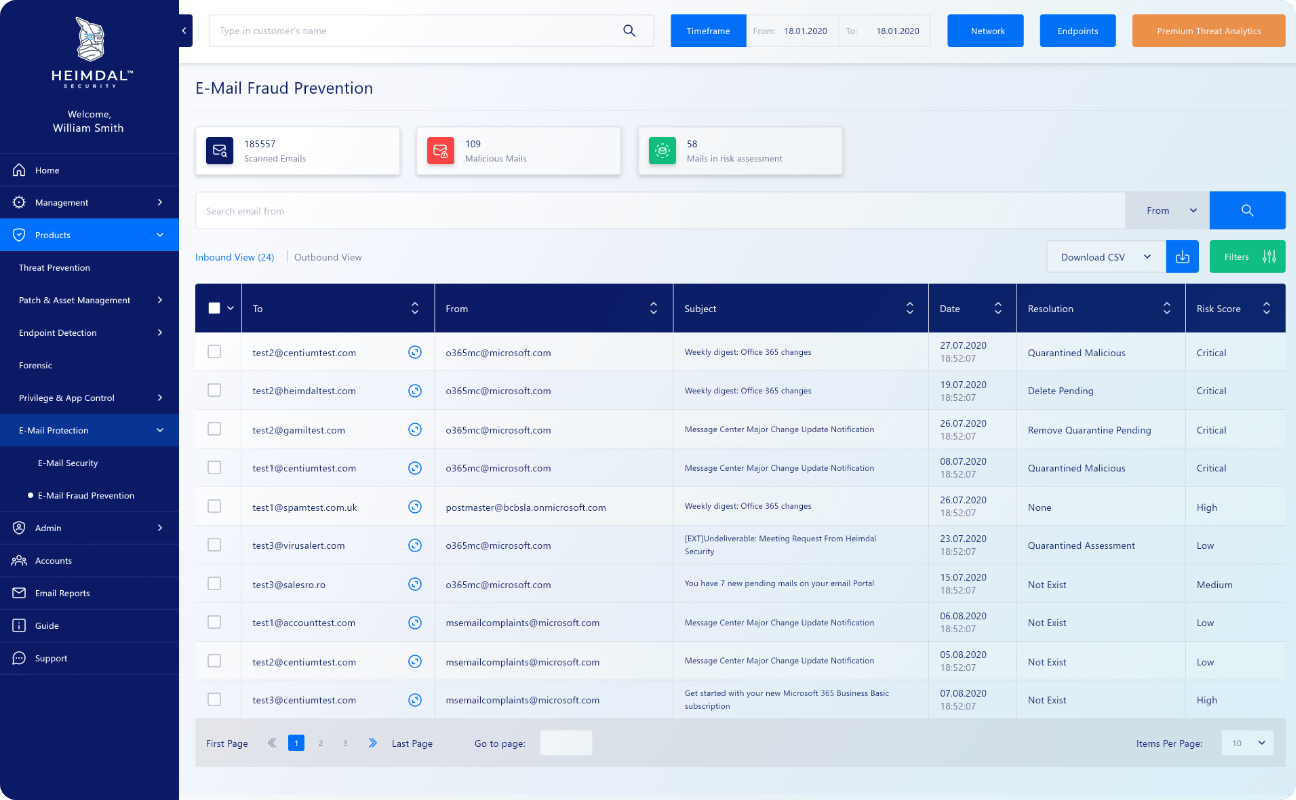
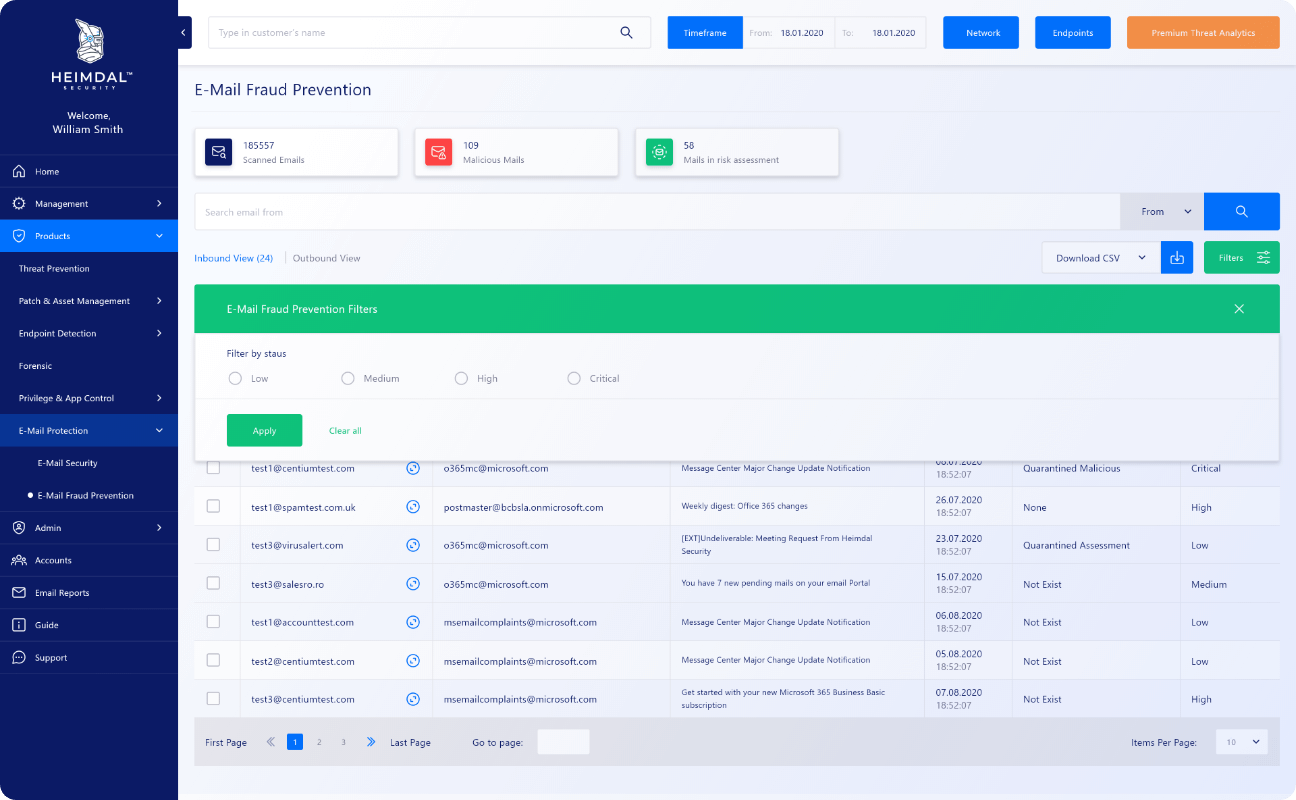
 Heimdal™ Email Fraud Prevention is an advanced email fraud prevention solution focusing on email alterations and potentially malicious email alterations with external invoice approval support through dedicated API for increased protection against CEO fraud, Business Email Compromise, phishing, and advanced malware.
Heimdal™ Email Fraud Prevention is an advanced email fraud prevention solution focusing on email alterations and potentially malicious email alterations with external invoice approval support through dedicated API for increased protection against CEO fraud, Business Email Compromise, phishing, and advanced malware.CENTRALIZED COMMAND CONTROL
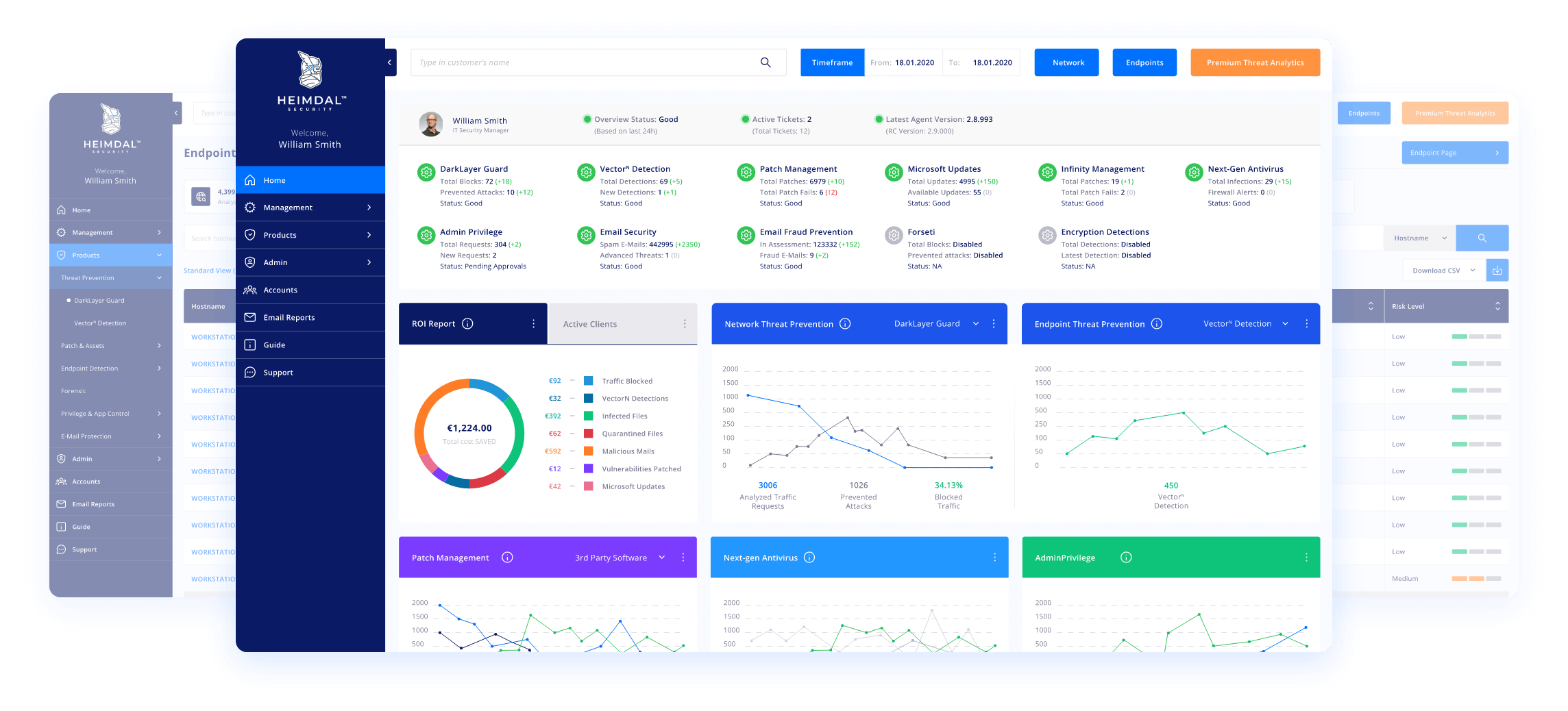
One Unified Dashboard To Rule Them All.
The centralized dashboard unlocks the full potential of your threat-hunting engine and cyber-stance. Crisp graphics, intuitive controls, ready-to-download security status reports, ROI outlooks, mitigated threats, CVEs, and more conveniently stacked into a responsive and unified dashboard.