Threat Prevention Network
Threat Prevention Network
Kodas: 11250Y1Kaina 2033 € su PVMŠią prekę turime sandėlyje.GamintojasHeimdal Security-
Threat Prevention – NetworkNetwork Perimeter DNS SecurityHunt, Prevent, Detect and Respond to any Network and IoT threat. Heimdal™ Threat Prevention - Network allows you to confidently own your BYOD governance and secure all your users' devices.



Prevent Tomorrow’s Threats Today.
Not just on your endpoints, but on any other devices.
Complete Device Coverage
Regain your peace of mind with a complete solution that spans across your business ecosystem. Protect and maintain BYODs, IoTs, and every other equipment linked to your company’s network.
Top-level Network Logging
Stay on top of your network traffic activity with Threat Prevention-Network’s logging tool. See what everyone is up to and prevent attacks before they land on your endpoints.
Threat-Hunting Made Easy
Threat Prevention – Network can be set up in seconds, with no additional software installation required. Say goodbye to hard-to-deploy threat-hunting solutions, with limited results and zero upscaling factor.KEY BENEFITS
Unique Solutions for Advanced ProblemsUnleash comprehensive threat hunting capabilities.
Leverage a Host-Based Intrusion Prevention System (HIPS), augmented by a highly intelligent threat detection technology powered by AI.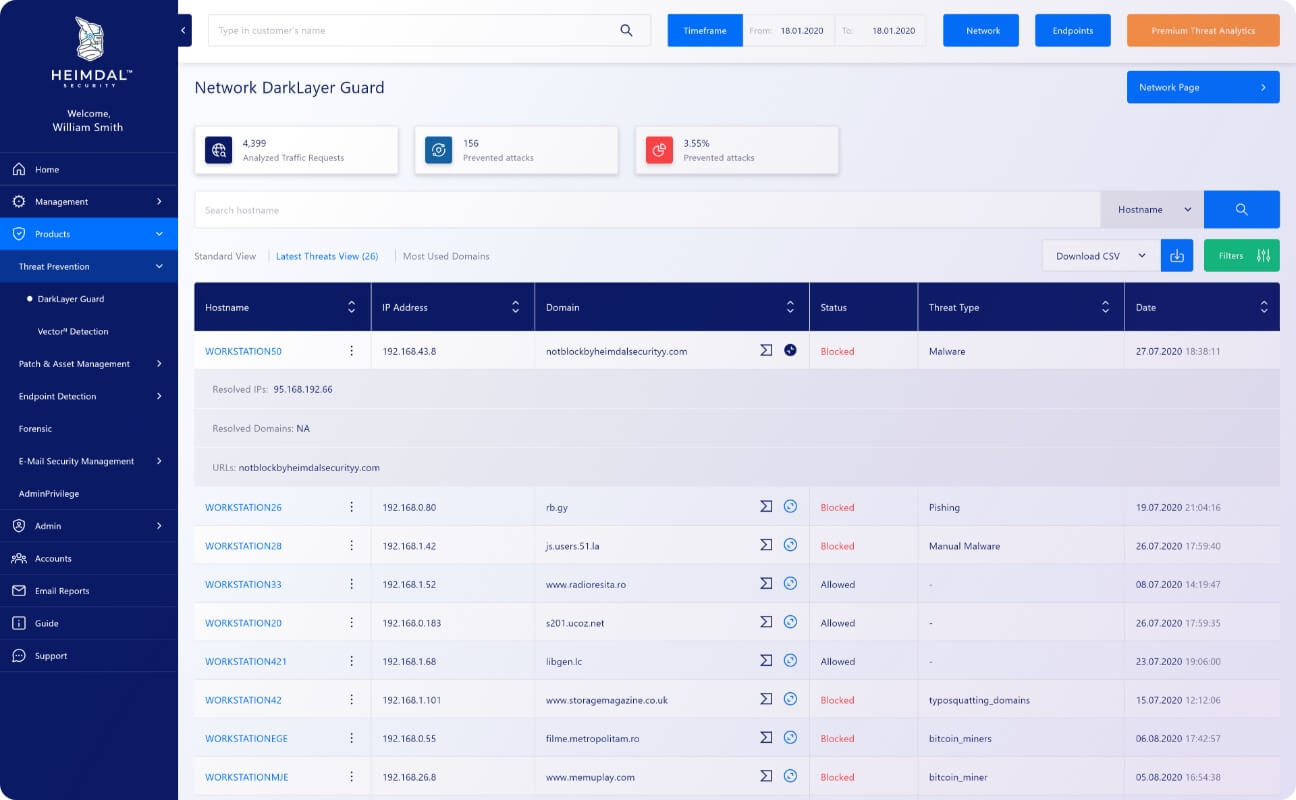
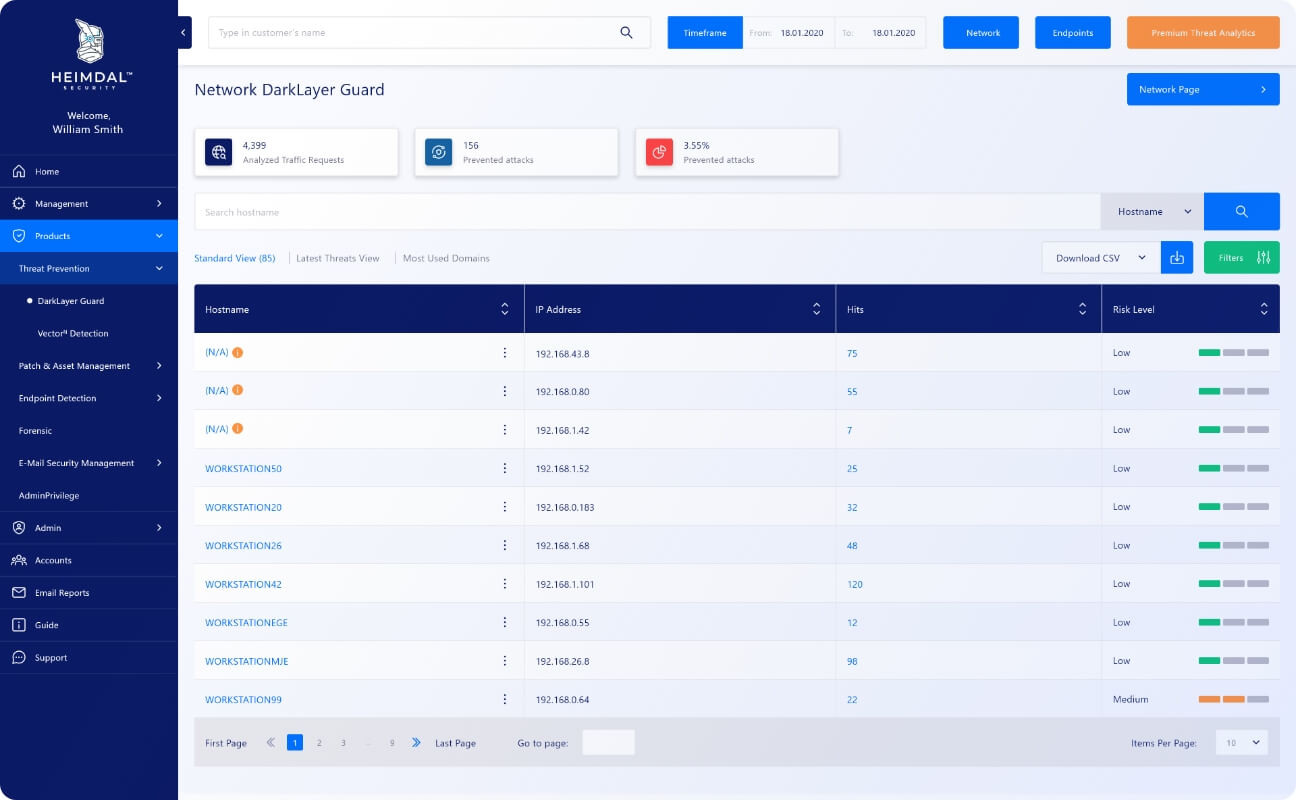 Empowering comprehensive detection and response
Empowering comprehensive detection and response
Threat Prevention - Network utilizes Cloud Access Security Brokerage (CASB) for increased security against malicious activities, granting extended cloud app curation granularity and empowering your IT admins to identify, classify, and eliminate unsanctioned apps from your cloud environment.Impeccable detection & prediction rates
Hunt, prevent, detect and respond to endpoint, network, and IoT threats with a 96% accuracy in detecting and predicting future attacks.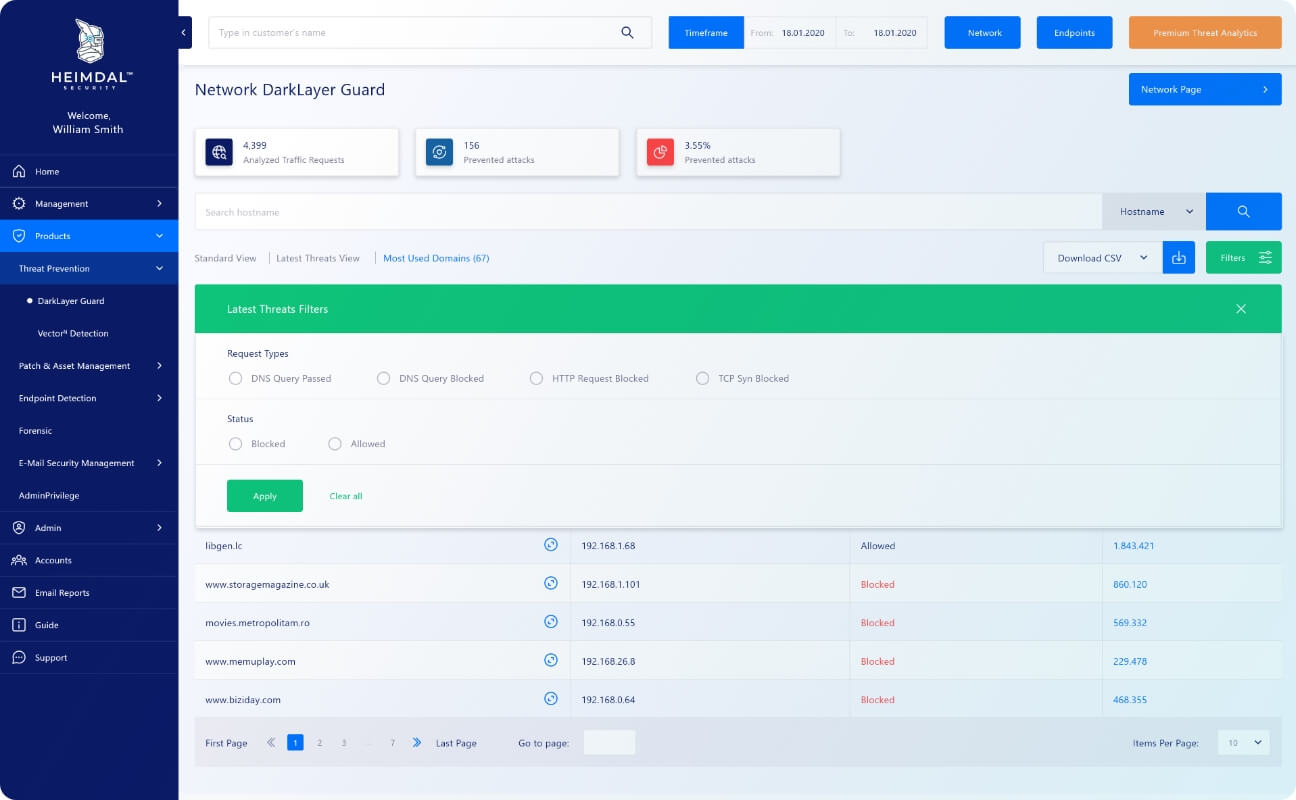
 Heimdal™ Threat Prevention - Network adds to any Antivirus, Firewall, IDS, or IPS and can be combined with more Heimdal™ products to deliver an authentic Endpoint Prevention, Detection, and Response (EPDR) stance. One agent, one platform.
Heimdal™ Threat Prevention - Network adds to any Antivirus, Firewall, IDS, or IPS and can be combined with more Heimdal™ products to deliver an authentic Endpoint Prevention, Detection, and Response (EPDR) stance. One agent, one platform.CENTRALIZED COMMAND CONTROL
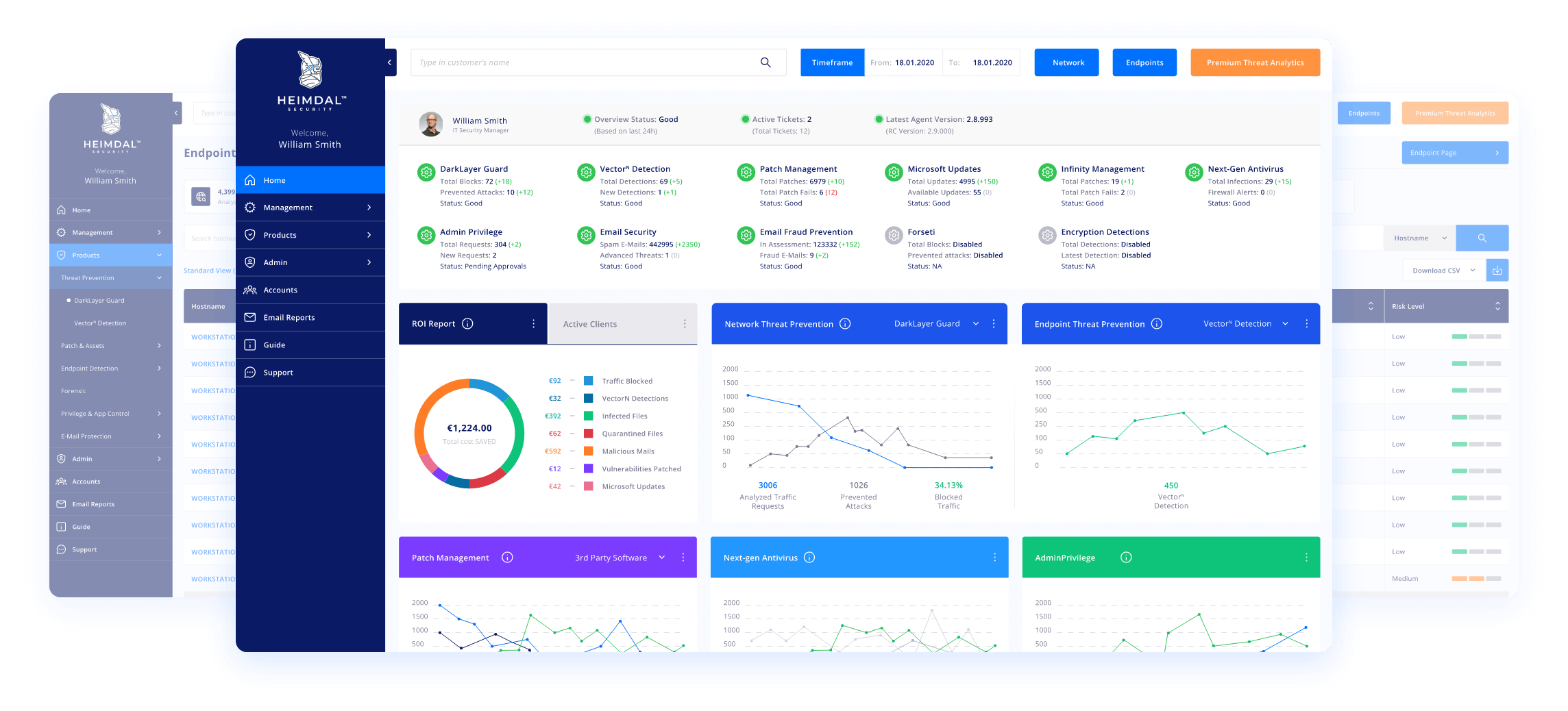
One Unified Dashboard To Rule Them All.
The centralized dashboard unlocks the full potential of your threat-hunting engine and cyber-stance. Crisp graphics, intuitive controls, ready-to-download security status reports, ROI outlooks, mitigated threats, CVEs, and more conveniently stacked into a responsive and unified dashboard.